QUICK CISCO AUDIT
While cisco is a vendor specific
product, the brand-name has become synonymous
with networking. So for better or worse, you will at some stage
probably need to audit a cisco configuration file. Now there are some
easy ways to do this, but I just want to explain some cavaets:
- What follows will never be as good as a knowledgeable 'human'
review
- What follows will not be of much use for the extreme high-end
cisco enterprise products
- Because what follows describes an automated process, always
review findings
Ok, with such dire warnings why
would you want to go any further?
Because while gaining competence with cisco is never a bad thing,
sometimes you just do not have the time and/or you need some quick
answers - kinda like running nmap rather then manually using telnet
.... just kidding.
Now to start with you need a cisco
config, you can get this by dumping
the output of the "show run"
command. This dump file will be a list of
all the settings that make your cisco device function just the way you
hope it should. Now for the tool. The tool that is famous for this type
of work is a tool called "nipper".
Now this tool was open-source, but a
while ago it went commercial. You can purchase the commercial tool
obviously, but I am cheap and you can still find the previous
open-source versions (see here,
here and here).
Once you extract the zip file you will have the nipper.exe binary.
Running "nipper --help", will
give you a bunch of the different options
but lets just keep it simple for now. Lets run it against our
configuration dump file..
Simple. Now if you take a look at
your you will see a whole bunch of
data, all very useful to pore over, but for now just take a look at the
sections (the 2.x sections) which show any identified risk areas. You
should see something like..
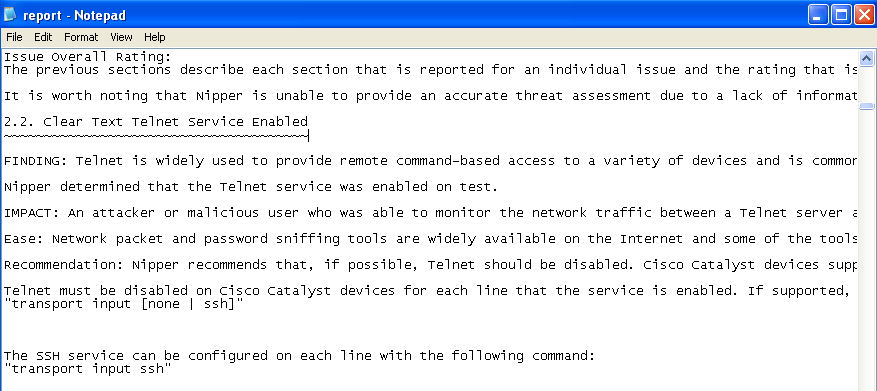
Nice! Now please, you should go
through these findings just as a sanity check - automated tools are
never 100%.
But what if you have lots of config
files to go through at one time? Is that easy? Why yes, yes it is.
- Put all your config dump files into the same folder as the nipper
binary (because I am lazy)
- Run this dos command in that folder: for %X in (*.txt) do (nipper --text
–-input=%X –-output=%X-rpt.txt)
- That will create a report file for each config file.
- Now download the UnxUtils
(here), these are linux binaries ported over to
windows binaries (again because I am lazy)
- From that zip, extract the grep.exe,
cut.exe, sort.exe, uniq.exe binaries to the nipper folder
- Run this dos command: grep -H
", 2\." ./*.txt-rpt.txt | cut -f 1-3 -d "," > list.txt
- This will pull all different security issues into one file
as well as which configuration file it is from
- Now run this dos command: type
list.txt | cut -f 2 -d ":" | sort | uniq > ./threat.txt
- This creates a simple list of all threats
- Now run this:for /f
"delims=: tokens=1" %X in (threat.txt) do (echo %X >> rpt.txt)
&& (@grep "%X" list.txt | cut -f 1 -d ":" >> rpt.txt )
&& (@echo ================= >> rpt.txt)
- This will create a report file (rpt.txt)
that list each security issue found followed by a list of configuration
files relevant to that issue
- Now copy/paste/massage the data as needed
Final Words
Nipper can do a lot more, but for a
quick check through, it can make your life a lot easier .... just a
pity about the whole "going commercial" thing. Anyway, have fun, play
and learn.

