Port
Scanning 101
Author - Natalia Wadden
Matrix Reloaded, Bourne Ultimatium and a brief glimpse in Girl with the
Dragon Tattoo – these are just a few movies which feature a port
scanning technique called nmap.
Before we go to far, let’s define nmap. It sounds glamorous, it
must be, it is featured in at least 3 major Hollywood films. Nmap
aka Network Mapper is a security scanner that is used to detect hosts
and services on a computer network – in short it can determine which
ports are open, what the operating system (OS) and version is, services
that are offered, and what firewalls are used – basically it can create
a map of the computer network and hosts.
Nmap is portable, it can be used across multiple platforms, Windows,
Mac and Linux, but it is most commonly used in Linux. For this
article, I will be using Kali Linux, it’s easy and many tools are
already built into the OS. My mentor described ports as windows
in a building, which means that nmap is looking for the open windows
aka ports. So let’s dive in and scan our test machine and see if
we can find any open ports.

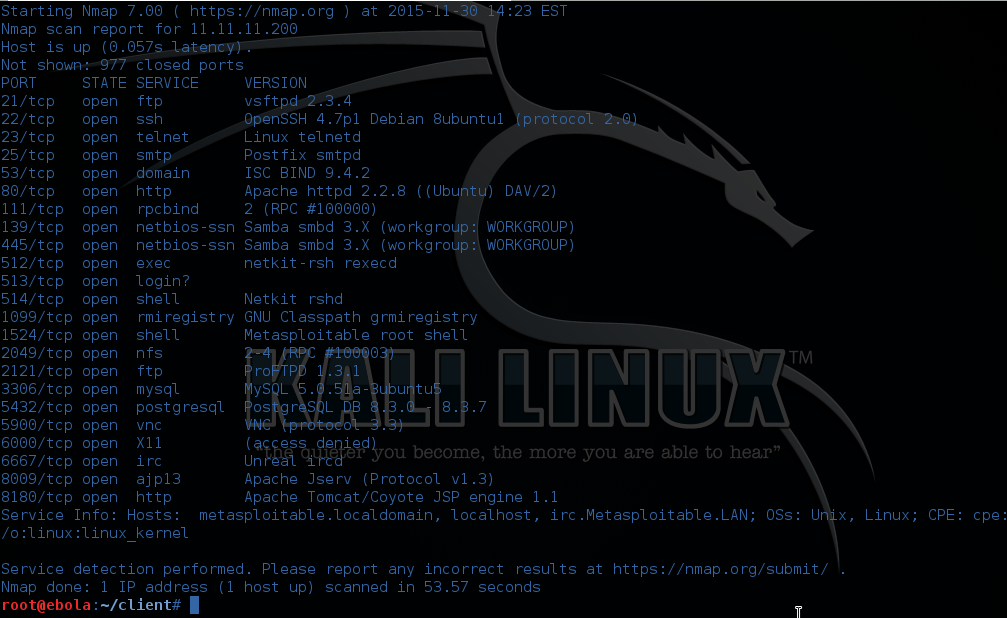
Our simple nmap scan provided us with a significant amount of
information, this can be over whelming if you don’t know what to
look for – let’s try to break it down. Nmap has shown us that each
of these ports are open via the 3 way TCP handshake. A SYN was
sent to an open port, in the case above port 80 (web) and responded
with a SYN ACK, the client answered SYN ACK with an ACK, thereby
completing the response. An open port 80 is not uncommon, many
websites have this open as they require it as part of their business,
for example, Amazon, Ebay and Google, all have port 80 open, if they
weren’t open nobody could see their website.
Now let’s try this again but use a UDP (User Datagram Protocol)
scan along with nmap, and see what happens. UDP scan does not
require the 3 way handshake, which means a request will be sent out,
but a response is not necessairly received, there is no guarentee of
delivery. UDP is typically used for streaming audio media and
real-time
video as it is designed to handle occasional lost packets, so only
slight degradation in quality occurs, rather than large delays if
lost packets were retransmitted.

The results of our UDP nmap scan above provides us with a datagram of
possible vulnernabilities, ports which if we were curious could
continue investigating, such as Port 53, Port 69 , Port 137 and Port
2049 – if we listen to these ports, we potentially might be
pleasantly surprised with what we find. Let’s do one more, let’s see if we can find out what versions are
running on each port.
Let’s try another one, this time,
this time, type in nmap man, this will bring up the nmap manual.
In our next example, let’s try a built-in shorthand for the most
popular options "-A". This type of scan provides additional
information about the remote system to the ports provided by a typical
nmap scan.
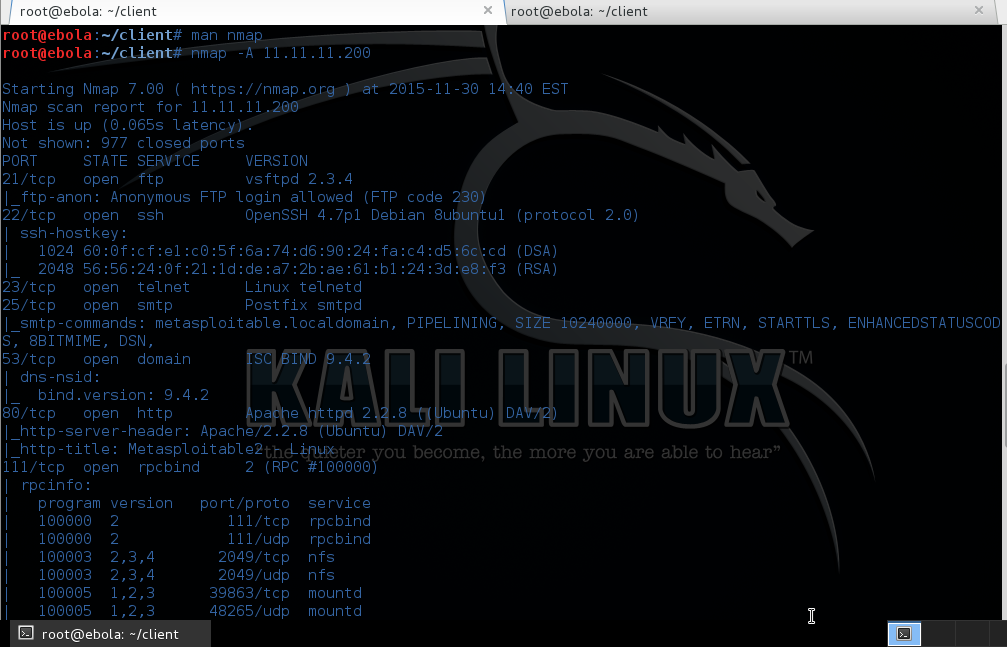
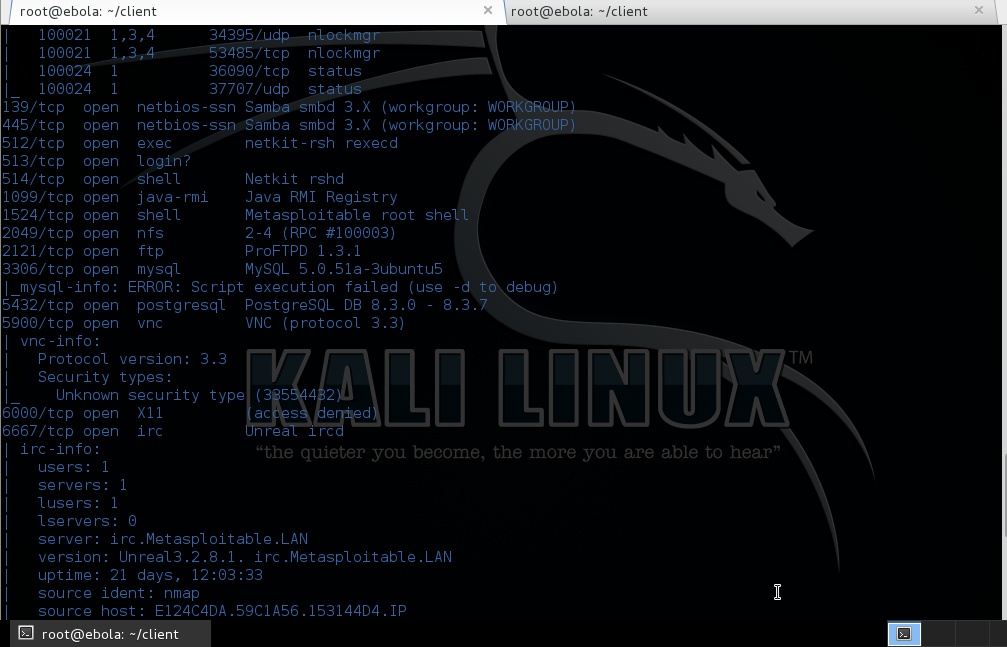
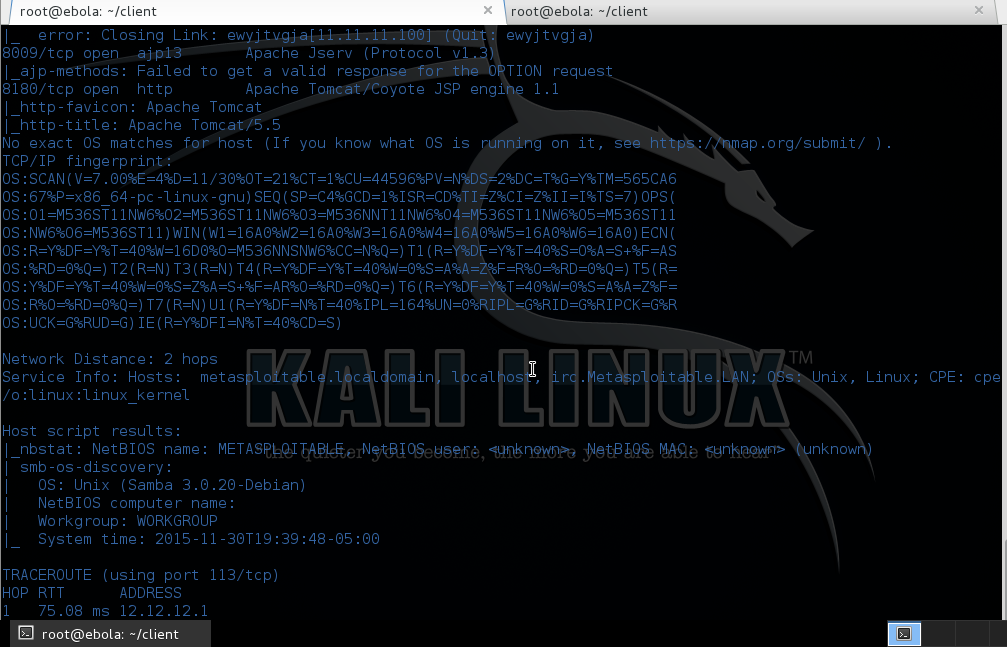
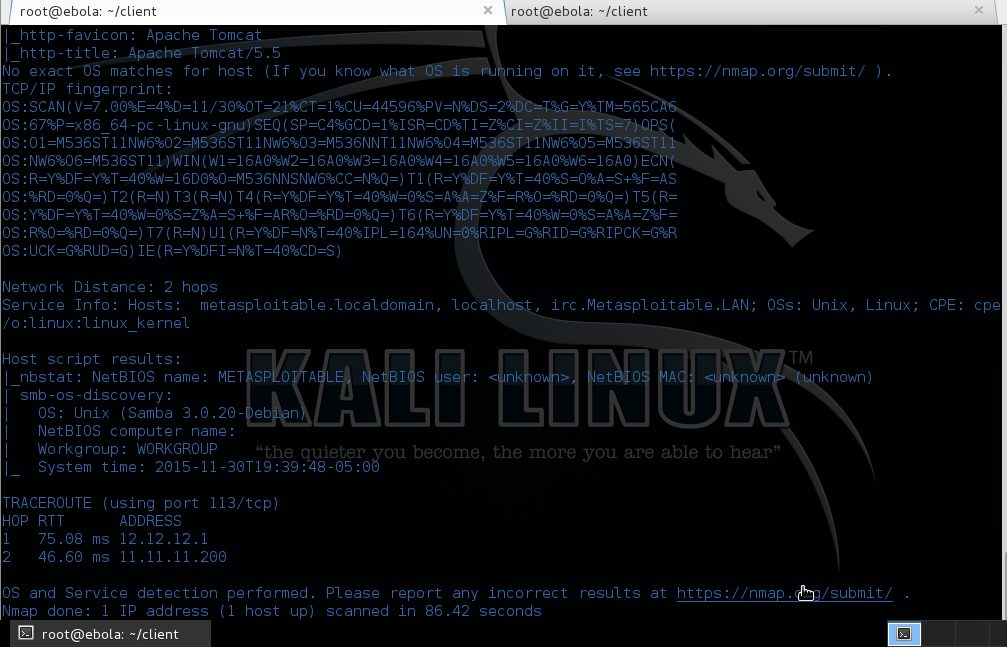
Take a close look at the results of
our scan - With a simple command, we have now discovered the OS
version, the various hosts as well as the version of Tomcat.
Nmap is used by many individuals,
and not all of them are “bad”, some are malicious individuals looking
to sniff around networks looking for open ports, to get information,
others are security professionals, using nmaping to conduct penetration
testing to safely exploit system vulnerabilities to evalute the
security.






